防火墙Trust区域访问互联网的NAT设置基础教程
上一节我们配置了内网用户访问DMZ区域,今天我们来配置一下内网用户访问互联网!
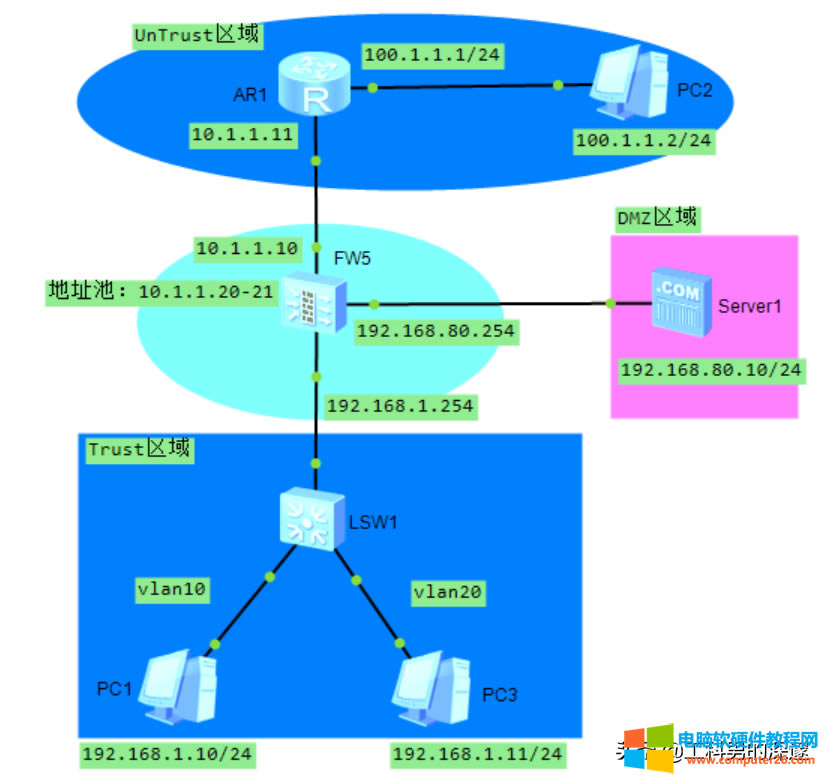
首先配置好各接口IP地址,并将接口加入到相应的安全区域内
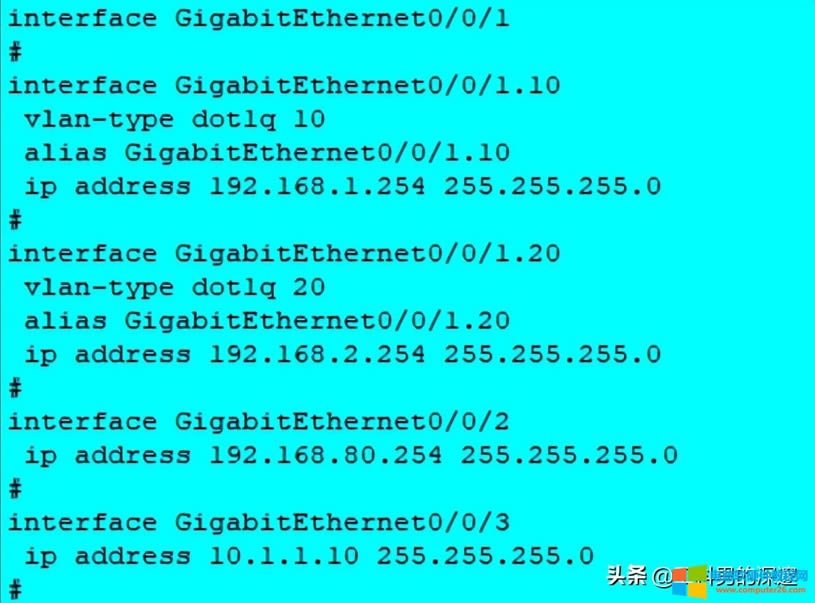
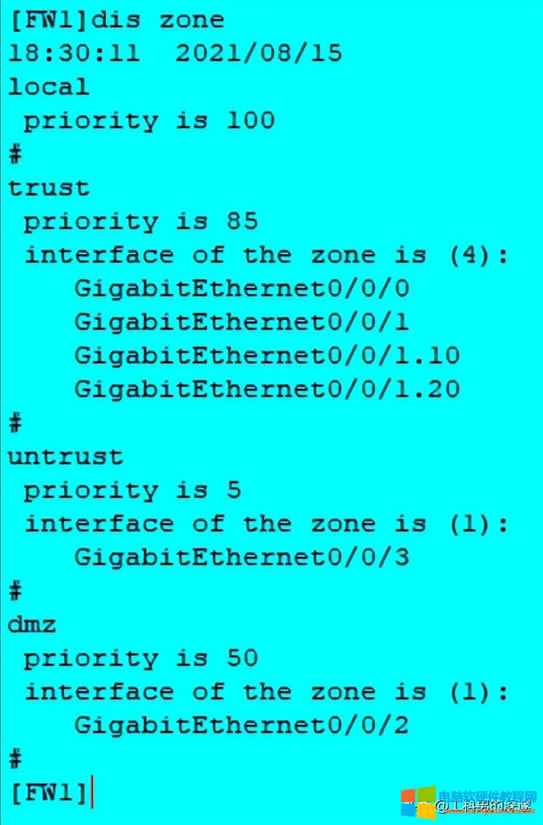
配置Trust用户访问互联网UnTrust
1、创建地址池
[FW1]nat address-group 1 10.1.1.20 10.1.1.21//配置NAT转换公网地址池;
2、配置NAT策略
[FW1]nat-policy interzone trust untrust outbound
[FW1-nat-policy-interzone-trust-untrust-outbound]policy 10
[FW1-nat-policy-interzone-trust-untrust-outbound-10]action source-nat
//配置源NAT转换,也可以配置no-pat模式;
[
FW1-nat-policy-interzone-trust-untrust-outbound-10]policy source 192.168.2.0 mask 24 (某一段地址)
[
FW1-nat-policy-interzone-trust-untrust-outbound-10]policy source 192.168.1.10 0(允许单个主机放行)
[FW1-policy-interzone-trust-untrust-outbound-20]policy destination any
3、配置源NAT地址转换
[
FW1-nat-policy-interzone-trust-untrust-outbound-10]address-group 1//关联地址池,使用端口复用PAT模式;若使用动态NAT,多对多模式,配置下列命令:
4、No-Pat地址转换
[
FW1-nat-policy-interzone-trust-untrust-outbound-10]address-group 1 no-pat//No-pat不进行端口转换,只进行地址转换,表示一对一转换,一个公网对应一个私网地址;
5、配置Trust到untrust安全策略并放行
[FW1]policy interzone trust untrust outbound
[FW1-policy-interzone-trust-untrust-outbound]policy 20
[
FW1-nat-policy-interzone-trust-untrust-outbound-10]policy source 192.168.1.0 mask 24 (放行转换之前的地址,某一段地址)
[FW1-policy-interzone-trust-untrust-outbound-20]policy service service-set icmp//不配置表示允许所有;
[FW1-policy-interzone-trust-untrust-outbound-20]action permit
[FW1-policy-interzone-trust-untrust-outbound-20]q
[FW1-policy-interzone-trust-untrust-outbound]q
[FW1]
注意:按照数据包到防火的转发流程,先匹配安全策略,策略通过的话,再匹配源NAT。
6、检测配置
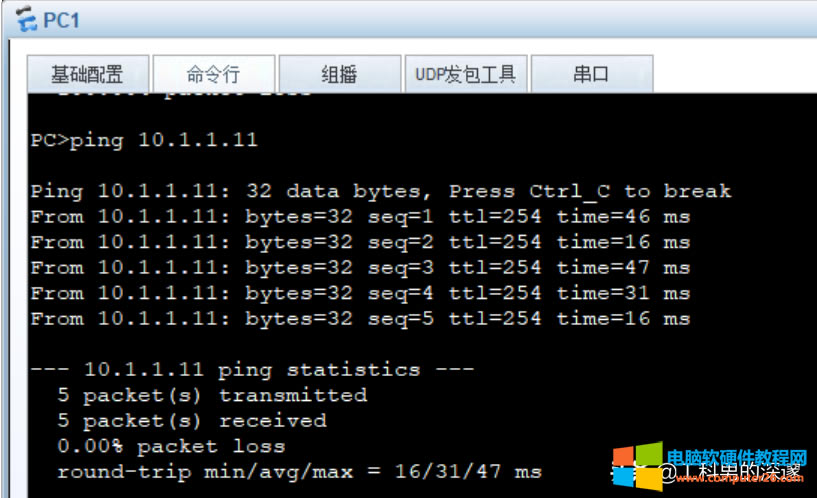
查看NAT策略
[FW1]display nat-policy all
[FW1]display nat-policy interzone trust untrust outbound
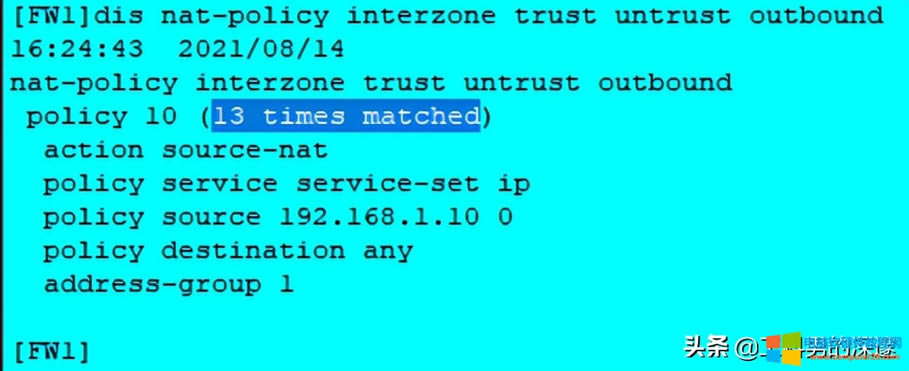
这个只有流量通过后,才能有数据;
[FW1]display firewall session table
检查安全策略
<FW1>display policy all
7、创建防火墙路由
[FW1]ip route-static 0.0.0.0 0.0.0.0 10.1.1.11
<FW1>display ip routing-table protocol static
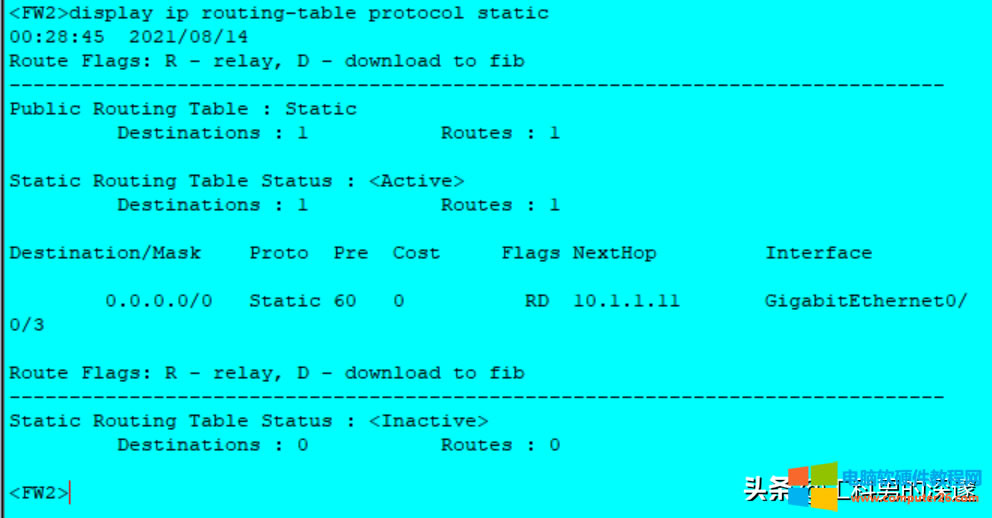
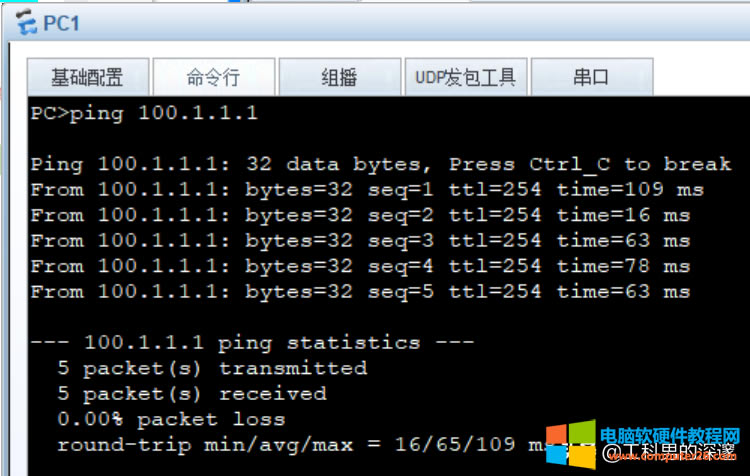
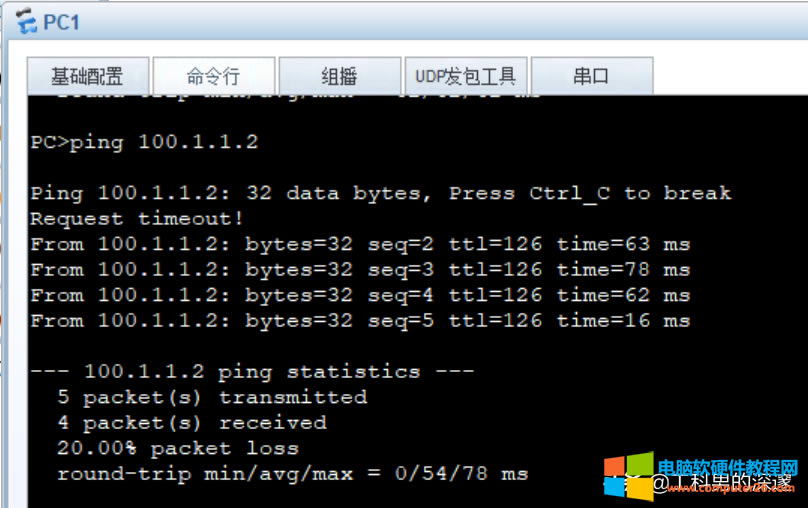
8、测试内部终端到公网PC
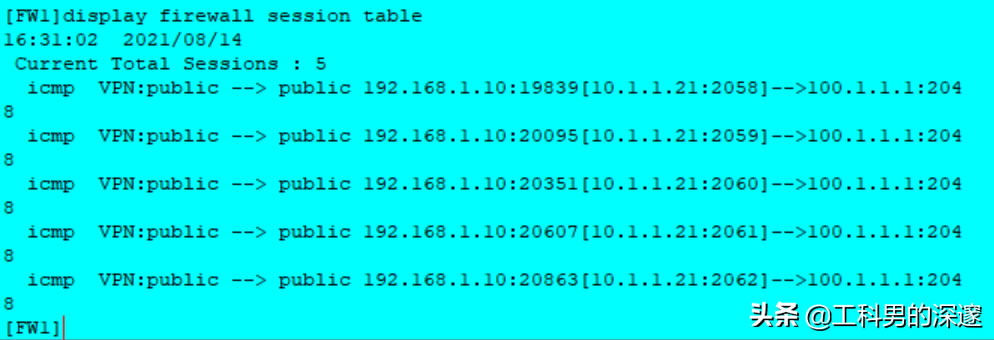
9、查看会话表
<FW1>display firewall session table
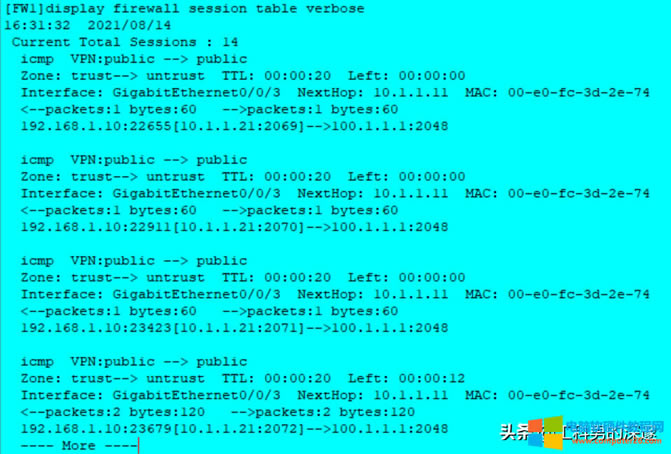
10、查看会话表详细信息
<FW1>display firewall session table verbose
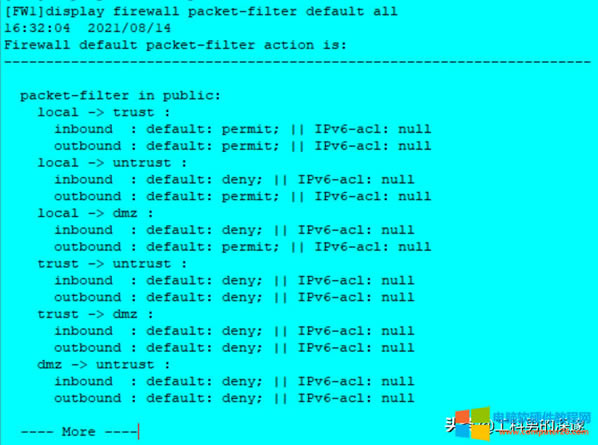
[FW1]display firewall packet-filter default all